App진단을 다시 시작해야하는데 Drozer 사용법을 까먹어버려 이번기회 정리하려고한다.
내 Drozer 사용법은 우회하여 기능실행할 수 있는지에 대한 사용으로 Drozer를 통해 강제로 화면을 호출할 때 실행해본다.
Drozer의 공식 사이트는 다음의 주소는 아래와 같다.
https://labs.withsecure.com/tools/drozer
Welcome to WithSecure Labs - Cyber security research and development
WithSecure Labs puts you at the forefront of innovation and research in cyber security.
labs.withsecure.com
가이드북에 따르면 Drozer설치에는 다음의 것들이 필요하다

이후 Drozer사이트에서 msi를 설치하여 다음 경로를 입력해 python2.7경로를 넣어준다.
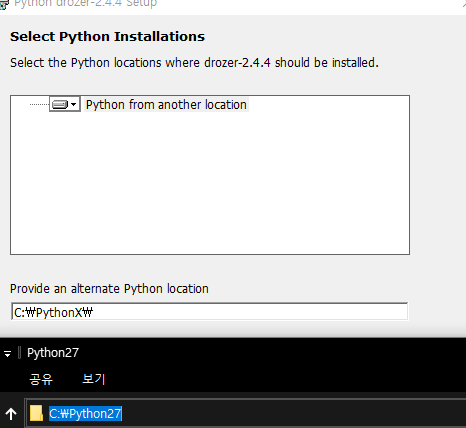
다음과 같이 drozer가 파이썬 안에 들어가면 성공
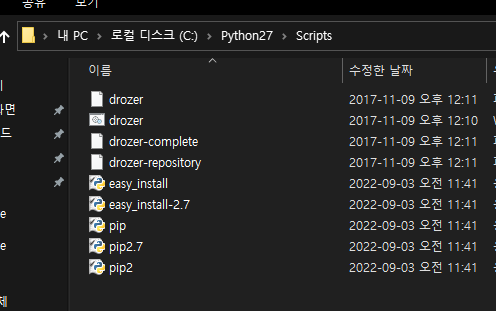
환경변수 넣어진거 확인하고
이후 cmd에 drozer를 통해 명령어 실행되면 설치 완료

다음은 drozer agent(apk파일)을 공식사이트에서 추가로 받고 진단할 android기기에 넣어준다(여기서는 nox)

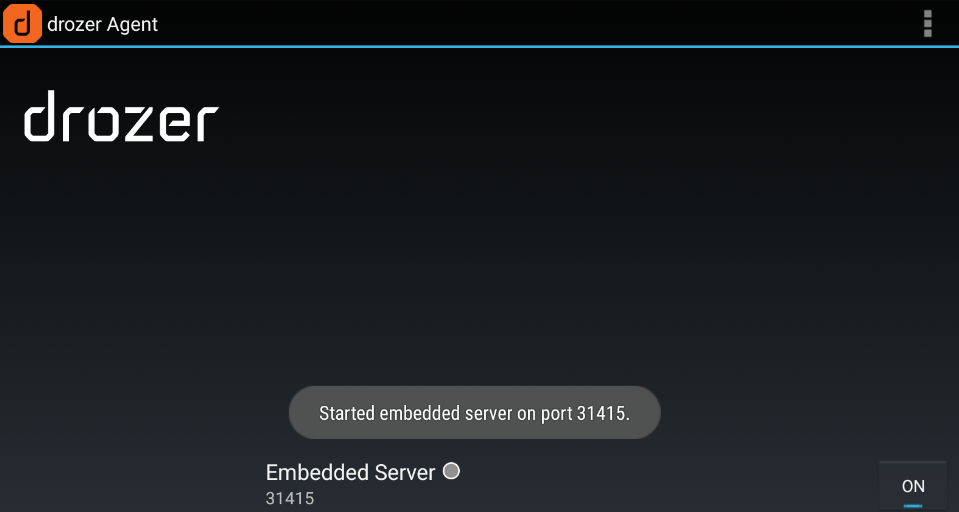
이후 drozer Agent 실행 후 포트와 on을 확인한다.
이후 adb를 통해 drozer 포트를 연결한다.($ adb forward tcp:31415 tcp:31415)

drozer console과 연결한다.(drozer console connect)
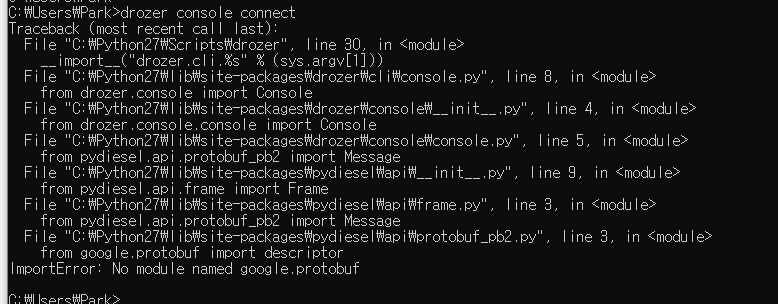
뭔가 에러가 떴고 좀 검색해보니 sdk의 문제인것같다(sdk는 studio설치후 다시 설치가 필요하다.)
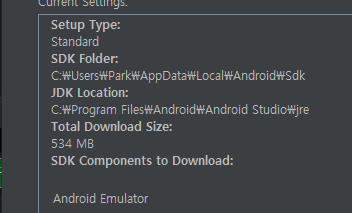
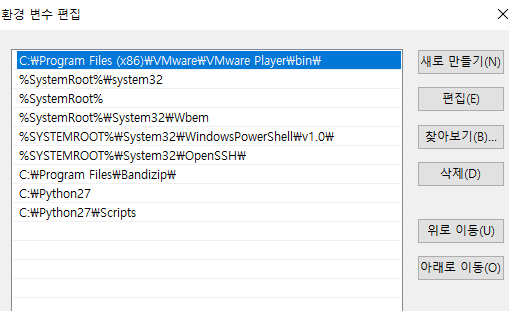
설치후 환경변수 추가로 다시 설정한다.

다음으로 필요한 라이브러리 설치해준다.
python -m pip install --upgrade pip
pip install setuptools
pip install google
pip install --upgrade google-api-python-client
pip install pyyaml
pip install protobuf
pip install pyOpenSSL
pip install twisted
pip install service_identity
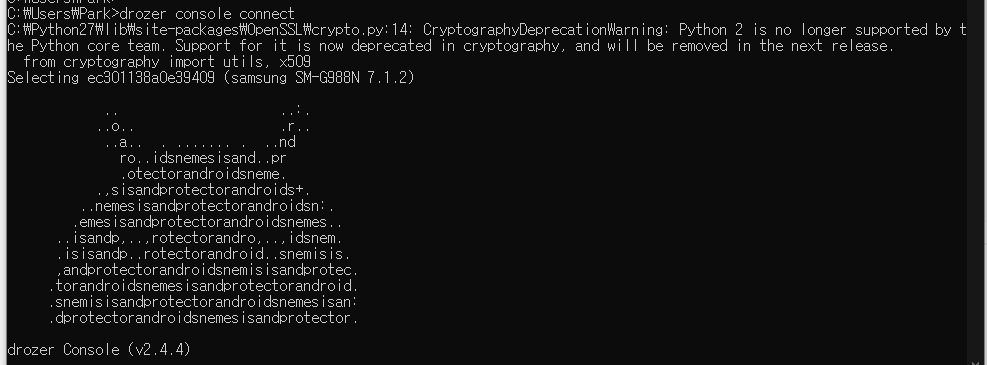
Drozer Console Connect후 저렇게 안드로이드 마크가 나오면 이제 끝이다.
먼저 list누르면 사용할수있는 패키지가 나온다.
app.activity.forintent Find activities that can handle the given intent
app.activity.info Gets information about exported activities.
app.activity.start Start an Activity
app.broadcast.info Get information about broadcast receivers
app.broadcast.send Send broadcast using an intent
app.broadcast.sniff Register a broadcast receiver that can sniff particular intents
app.package.attacksurface Get attack surface of package
app.package.backup Lists packages that use the backup API (returns true on FLAG_ALLOW_BACKUP)
app.package.debuggable Find debuggable packages
app.package.info Get information about installed packages
app.package.launchintent Get launch intent of package
app.package.list List Packages
app.package.manifest Get AndroidManifest.xml of package
app.package.native Find Native libraries embedded in the application.
app.package.shareduid Look for packages with shared UIDs
app.provider.columns List columns in content provider
app.provider.delete Delete from a content provider
app.provider.download Download a file from a content provider that supports files
app.provider.finduri Find referenced content URIs in a package
app.provider.info Get information about exported content providers
app.provider.insert Insert into a Content Provider
app.provider.query Query a content provider
app.provider.read Read from a content provider that supports files
app.provider.update Update a record in a content provider
app.service.info Get information about exported services
app.service.send Send a Message to a service, and display the reply
app.service.start Start Service
app.service.stop Stop Service
auxiliary.webcontentresolver Start a web service interface to content providers.
exploit.jdwp.check Open @jdwp-control and see which apps connect
exploit.pilfer.general.apnprovider Reads APN content provider
exploit.pilfer.general.settingsprovider Reads Settings content provider
information.datetime Print Date/Time
information.deviceinfo Get verbose device information
information.permissions Get a list of all permissions used by packages on the device
scanner.activity.browsable Get all BROWSABLE activities that can be invoked from the web browser
scanner.misc.native Find native components included in packages
scanner.misc.readablefiles Find world-readable files in the given folder
scanner.misc.secretcodes Search for secret codes that can be used from the dialer
scanner.misc.sflagbinaries Find suid/sgid binaries in the given folder (default is /system).
scanner.misc.writablefiles Find world-writable files in the given folder
scanner.provider.finduris Search for content providers that can be queried from our context.
scanner.provider.injection Test content providers for SQL injection vulnerabilities.
scanner.provider.sqltables Find tables accessible through SQL injection vulnerabilities.
scanner.provider.traversal Test content providers for basic directory traversal vulnerabilities.
shell.exec Execute a single Linux command.
shell.send Send an ASH shell to a remote listener.
shell.start Enter into an interactive Linux shell.
tools.file.download Download a File
tools.file.md5sum Get md5 Checksum of file
tools.file.size Get size of file
tools.file.upload Upload a File
tools.setup.busybox Install Busybox.
tools.setup.minimalsu Prepare 'minimal-su' binary installation on the device.
이후 실제 사용음 다음글부터
'업무 > APP(AND)진단 쉽게하려 만든 게시판' 카테고리의 다른 글
| androguard를 사용한 APK 쉽게 권한 추출하기 (0) | 2022.09.03 |
|---|---|
| Android 진단도구 Drozer(#2) (0) | 2022.09.03 |
| Drozer (0) | 2021.11.30 |
| android 원격 쉘 연결 방법 (0) | 2021.10.28 |
| Android 진단도구 Drozer (0) | 2021.10.28 |